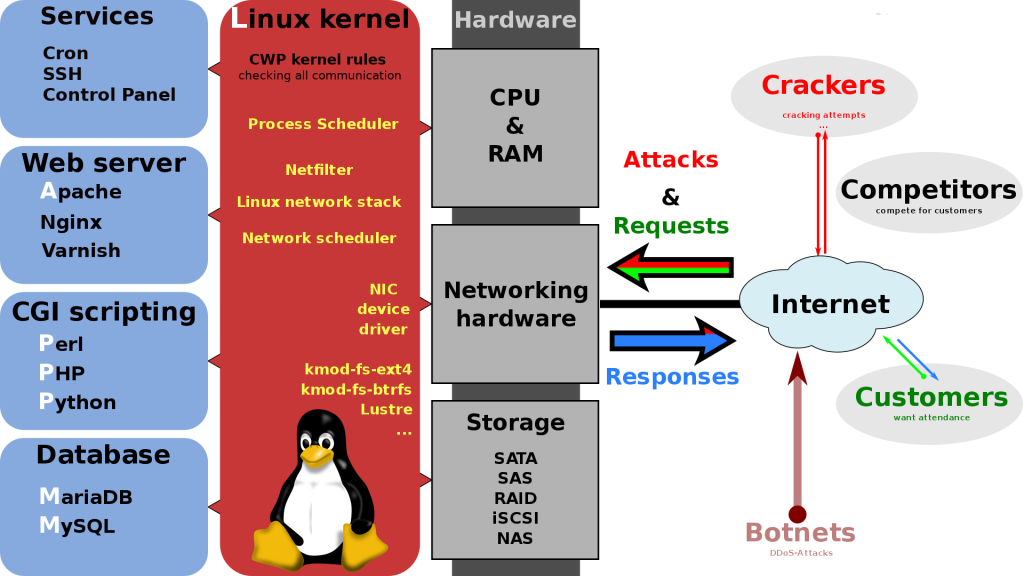
CWP Secure Kernel checking each action and request:
Video instructions
CWPsecure kernel when in use provides the highest security possible on the market for the shared hosting, no other control panel has something similar integrated to compare with. We can only compare it with Cloudlinux/CageFS.
CWP custom kernel with security level similar to SeLinux.
Since this protection is MAC at the kernel level meaning all not allowed by the policy by default is denied and that provides the highest security for your system.
Demo CWP Secure Kernel SSH account
SSH Server: 142.4.197.233
Username: cwpuser
Password: neQumXagNUTj
SSH Port: 19443
Example ssh login: ssh cwpuser@142.4.197.233 -p 19443
* You can test here all example commands, the demo account is reset every 1h.
Not supported systems: openVZ, cloudlinux, Virtuozzo, Lxc, Docker container
Requirement: Having the ability to run & install default centos kernel.
Supported OS el7: CentOS 7
Supported OS el8: CentOS Stream, CWP CentOS Delayed, Rocky Linux, Alma Linux, Oracle Linux
How does it work?
We need to define into policy each binary file that can be executed and specify the allow list of rules for it.
We can allow per application, user, program, service access to specif file, socket, port, IP ...
We can allow for example that the test.php file of the user "john" located at /home/john/public_html/test.php can be executed only by john user and only by php-cgi version 5.4 which needs to be run by the john user.
File Based restrictions (please note all not allowed, by default is denied)
file read
file write
file execute
file append
file truncate
file rename
file getattr
file create
file unlink
file symlink
file link
file chown
file chgrp
file chmod
file chroot
file mkdir
file rmdir
file mkfifo
file mksock
file mkblock
file mkchar
file ioctl
file mount
file unmount
file pivot_root
misc env
Network limits
These rules allow us to perform network socket operations.
network inet
Network limits
These rules allow us to perform Unix socket operations.
network unix
This protection can limit connection on the IP and/or port,
deny read/write/execute.... access to the files if the owner is not matched...
At the moment we have defined more than several thousand rules which work with cwp only.
A list of possible limits is huge so we can't add all info here.
INSTALLATION
Since this requires maintenance at the moment it's available only for our clients having an active support service: Managed, Business or Enterprise.
Clients having CWP with an active support service can request from the support team to get the CWP kernel deployed.
If you don't have a support service you can get it here.
Currently, the CWP kernel is protecting:
- cwp user panel
- apache webserver
- varnish web cache server
- nginx webserver
- user crons and all applications running as cron
- user ssh access
- all PHP versions available in CWP: switcher, selector, and PHP-FPM selector
...we are continuously developing additional rules to expand protection on many other services
Example issues which kernel is protecting you from:
- symlink attacks (most commonly used to hack all users on the server)
- execution of malware or custom scripts
- access to server system files (/etc,/var, /usr, /home, and all others)
- access to /tmp and /var/tmp files
- access to /dev/shm memory partition
- custom script connecting to other servers/ports
- malware cron running bad things
- hacked user ssh access to be used for running hacker scripts
- hacked user ssh access to be used for accessing the system files
- the limited set of secure tested ssh commands are only available to users
...and many others.
It's very important to run cwp secure kernel on Webhosting servers to protect your system from hackers and also to prevent hacker and malware to expand from one hacked website to multiple sites and users or even the full server.
NOTE: If you run some custom programs, binary files, or others you will need to make custom rules if running CWP Secure Kernel.
We are continuously maintaining the kernel and the configuration to keep your servers at the highest level of security.